Gain visibility into data across your organization
- Tellistic

- Jul 11, 2025
- 2 min read
The first part of securing your organization’s data is gaining visibility into the entire data estate. You’ve to know your data before you can put in steps to secure it. There are two steps to this. The first one is discovering your data. The second one is classifying your data. How do you go about these? There is a tool that can help you achieve these processes in a seamless manner.

Data discovery/identification
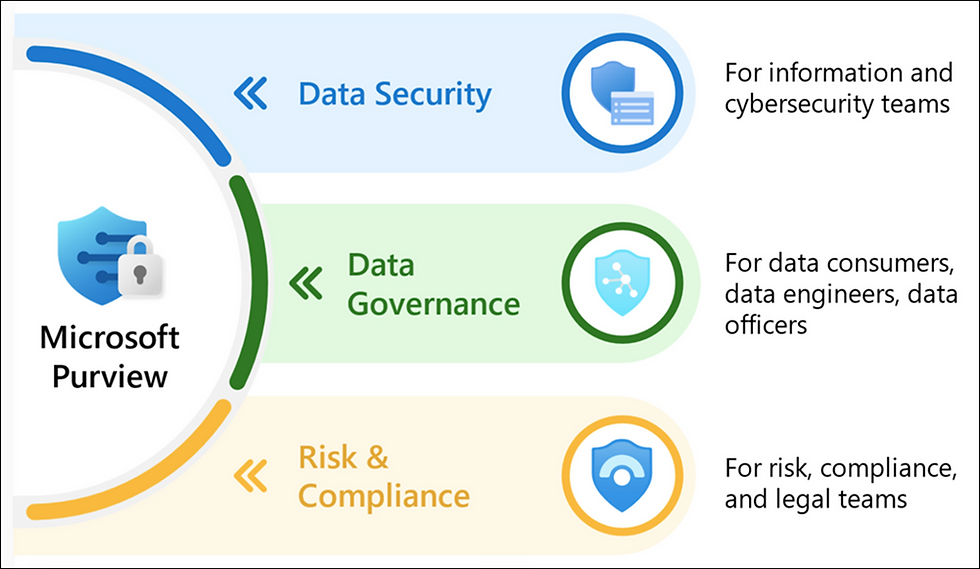
Microsoft Purview is a comprehensive set of solutions that can help you discover, classify, protect, govern and manage data in your organization. The tool’s Data Map solution helps you discover, register and scan your data sources. It also helps you map your entire data estate as well as identifying sensitive data. Sensitive data include intellectual property, customer data, operational data, and financial forecasts. This is the kind of data that an organization cannot afford to put at risk because of the resultant financial or reputational damage this can result into.
Data classification
After you identify your sensitive data, you need to classify it using sensitivity labels. You can give your data labels such as Public, Confidential, and Highly confidential depending on how sensitive it is. Data classification aims at classifying sensitive and business-critical data across the entire data estate by designating it with sensitivity labels.
Know your data
Your data security journey starts with knowing your data – so that you understand what sensitive information exists, where it lives, how of the sensitive data has been classified with labels. This will inform the protection settings to be enforced on the labelled data.
Conclusion
Data identification and data classification are beginning points of your data security journey. Understanding which data sources contain sensitive information is key to knowing where protections are needed and how to guard against access to the different types of sensitive data.
In our next article, we delve into how to apply protections to sensitive data across it lifecycle, wherever it lives in your organizations data estate. Stay tuned.



Comments